GitHub - magiclen/js-short-crypt: ShortCrypt is a very simple encryption library, which aims to encrypt any data into something random at first glance.

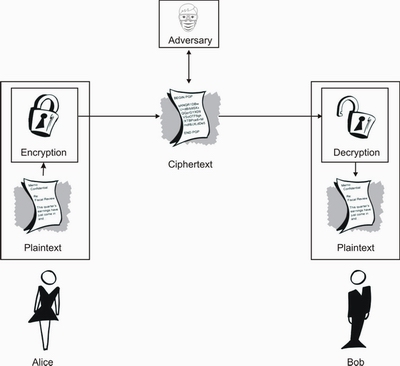
Figure1 shows the overall framework of encryption and decryption of the... | Download Scientific Diagram